
Intel is set to improve malware protection by incorporating what it calls Control-flow Enforcement Technology (CET) in its upcoming Tiger Lake processors. The tech giant marks a tweak in the way processors run instructions from applications, theoretically checking how memory is handling tasks and flagging up anomalies before they reach the OS. CET is devised to guard against the misuse of legitimate code through control-flow hijacking attacks, which is widely used in large classes of malware, the company representative explained.
Intel CET deals with the order in which operations are executed inside the Processor. Malware can use vulnerabilities in other apps to hijack their control flow and inject malicious code into the app, making it so that the malware runs as part of a legitimate application, which makes it very difficult for software-based anti-virus applications to detect. These are in-memory attacks, rather than writing code to the disk or ransomware. Intel cited TrendMicro’s Zero Day Initiative (ZDI), which said 63.2% of the 1,097 vulnerabilities disclosed by ZDI from 2019 to today were linked to memory safety.
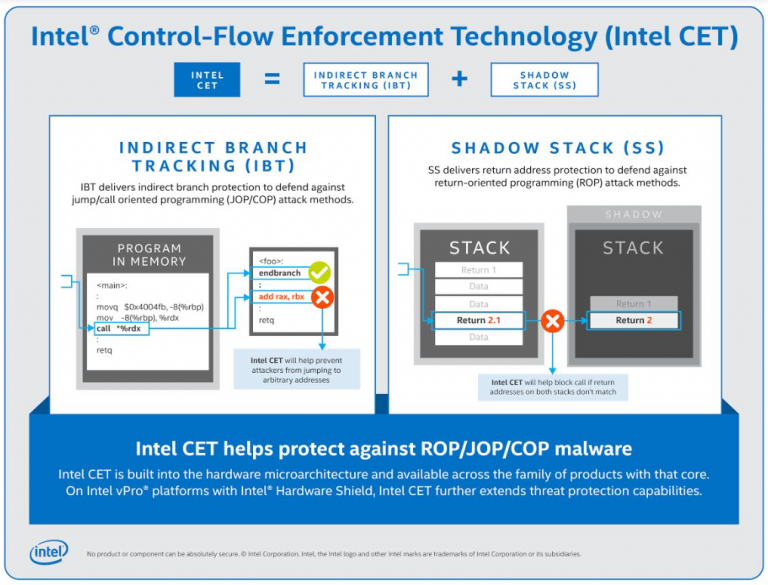
“Intel is saying, let’s look at some of the attacks that could happen and provide protections in hardware, so that the operating system, or security software, can be told by the the processor that this is worth looking at, it looks bad,” said Paul Ducklin from security company Sophos, adding that Inters CET should improve detection rates and lighten the load on software once companies write code to accommodate the technology.
CET shields the control flow via two new security mechanisms: shadow stack and indirect branch tracking. Shadow stack creates a copy of an app’s intended control flow and stores it in a protected area of the CPU to ensure no unauthorized alterations take place in an app’s intended execution order. The malware operates by hijacking an app’s proposed order of execution, so this prevents malware.






















